Cytomic Encryption module panels/widgets
Accessing the dashboard
From the top menu, select Status. From the side menu, select Cytomic Encryption.
Required permissions
You do not need additional permissions to access the widgets associated with Cytomic Encryption.
Encryption status
This widget shows the computers that support Cytomic Encryption and their encryption status.
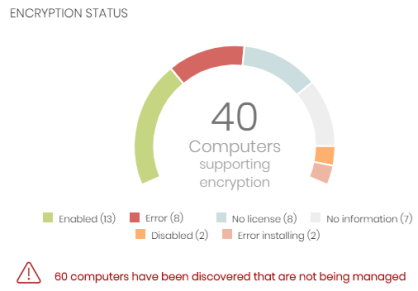
Meaning of the data displayed
Lists accessible from the panel
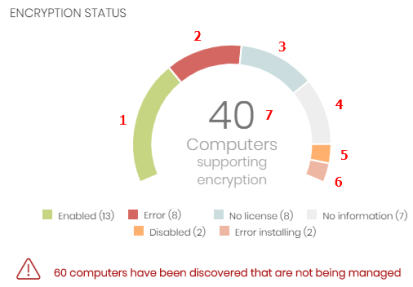
Click the hotspots shown in Hotspots in the Encryption Status panel to open the Encryption status list with these predefined filters:
Computers supporting encryption
This widget shows computers that support encryption technology, grouped by type. The color green indicates devices that support encryption, and the color red indicates devices that do not.
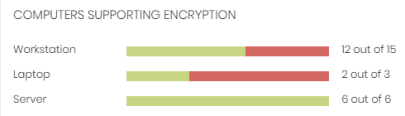
Meaning of the data displayed
| Data | Description |
|---|---|
|
Workstation - green |
Workstations that support encryption. |
|
Workstation - red |
Workstations that do not support encryption. |
|
Laptop - green |
Laptops that support encryption. |
|
Laptop - red |
Laptops that do not support encryption. |
|
Server - green |
Servers that support encryption. |
|
Server - red |
Servers that do not support encryption. |
Lists accessible from the panel

Click the hotspots shown in Hotspots in the Computers Supporting Encryption panel to open the Encryption status list with these predefined filters:
| Hotspot | Filter |
|---|---|
|
(1) |
Computer type = Workstation. |
|
(2) |
Computer list filtered by Encryption not supported. |
|
(3) |
Computer type = Laptop. |
|
(4) |
Computer list filtered by Encryption not supported. |
|
(5) |
Computer type = Server |
|
(6) |
Computer list filtered by Encryption not supported. |
Encrypted computers
This widget shows the encryption status of computers that support Cytomic Encryption.
For more information about how to search for recovery keys, see section Obtaining a recovery key.
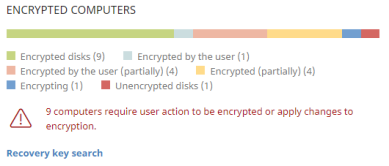
Meaning of the data displayed
| Data | Description |
|---|---|
|
Unknown |
Disks encrypted with an authentication method that Cytomic Encryption does not support. |
|
Unencrypted disks |
Neither the user or Cytomic Encryption has encrypted a disk. |
|
Encrypted disks |
Cytomic Encryption has encrypted all disks. |
|
Encrypting |
At least one disk is currently in the encryption process. |
|
Decrypting |
At least one disk is currently in the decryption process. |
|
Encrypted by the user |
A user encrypted some or all of the disks. |
|
Encrypted by the user (partially) |
A user encrypted some or all of the disks. Cytomic Encryption encrypts or decrypts the remainder. |
|
Encrypted (partially) |
Cytomic Encryption encrypted at least one of the disks. The remaining disks are unencrypted. |
Lists accessible from the panel
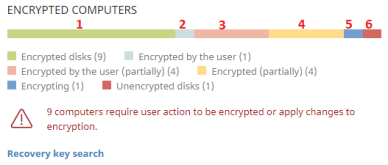
Click the hotspots shown in Hotspots in the Encrypted Computers panel to open the Encryption status list with these predefined filters:
| Hotspot | Filter |
|---|---|
|
(1) |
Disk encryption = Encrypted disks. |
|
(2) |
Disk encryption = Encrypted by the user. |
|
(3) |
Disk encryption = Encrypted by the user (partially). |
|
(4) |
Disk encryption = Encrypted (partially). |
|
(5) |
Disk encryption = Encrypting. |
|
(6) |
Disk encryption = Unencrypted disks. |
|
(7) |
Disk encryption = Decrypting. |
|
(8) |
Disk encryption = Unknown. |
Authentication method applied
This widget shows encrypted computers and the type of authentication used. For more information about the supported authentication methods, see General features of Cytomic Encryption.
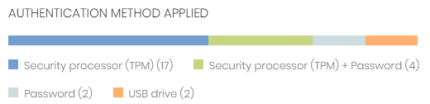
Meaning of the data displayed
Lists accessible from the panel
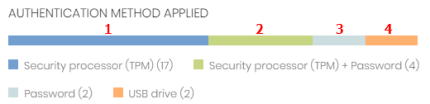
Click the hotspots shown in Hotspots in the Authentication Method Applied panel to open the Encryption status list with these predefined filters:
| Hotspot | Filter |
|---|---|
|
(1) |
Authentication method = Security processor (TPM) |
|
(2) |
Authentication method = Security processor (TPM) + Password |
|
(3) |
Authentication method = Password |
|
(4) |
Authentication method = USB drive |
|
(5) |
Authentication method = Unknown |
|
(6) |
Authentication method = None |