Allowing blocked items to run
Use these panels according to the type of blocked item you want to allow to run:
-
Currently blocked programs being classified: Unblock items in the process of classification.
-
Malware activity: Allow the execution of programs classified as malware.
-
PUP activity: Allow the execution of programs classified as PUPs.
-
Exploit activity: Allow the execution of exploit techniques.
-
Network attacks: Allow traffic classified as dangerous by the Network Attack Protection.
Unblocking items pending classification
In general, it is not recommended to allow the execution of unclassified items as this could pose a risk to the integrity of the company data and IT systems.
If users cannot wait for classification of an item, the administrator can unblock it manually.
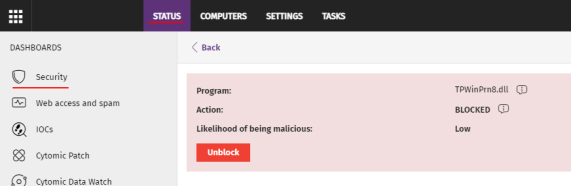
To allow the execution of an unknown item in the process of classification:
-
From the top menu, select Status. From the side panel, select Security.
-
Click the Currently blocked programs being classified panel and select the item you want to unblock from the list.
-
Click Unblock. A page opens to inform you of the risk of unblocking the unknown item and the assessment of its risk level.
-
Click Unblock. Advanced EDR performs these actions:
-
Allows the item to run on all managed computers on the IT network.
-
Allows all libraries and binary files used by the program to run, except those already known and classified as threats
-
Removes the item from the Currently blocked programs being classified list.
-
Adds the item to the Programs allowed by the administrator list.
-
Adds the item to the History of programs allowed by the administrator list..
-
Continues to analyze the item until it is classified.
-
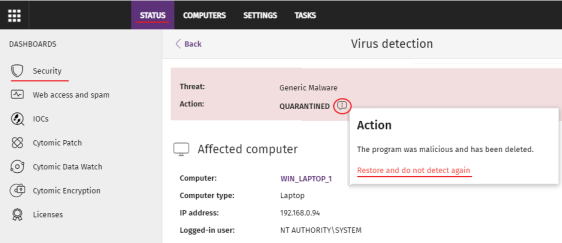
Allowing the execution of items classified as malware, PUP, or exploit
In general, it is not recommended to allow the execution of items classified as a threat, because this poses a clear risk to the integrity of the company data and IT systems.
If users need to use certain features provided by a program classified as a threat and the administrator considers that the danger posed to the integrity of the managed IT network is low, the administrator can allow the program.
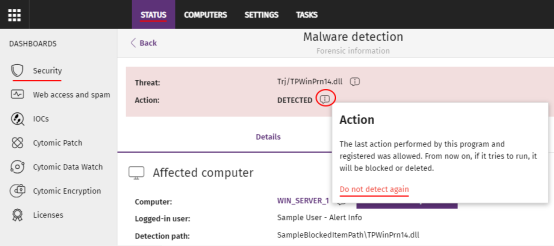
To allow execution of a program classified as malware, PUP, or exploit:
-
From the top menu, select Status. From the side panel, select Security.
-
Click the Malware activity, PUP activity, or Exploit activity panel and select the threat that you want to allow to run.
-
On the details page, click the
 icon next to the action. A pop-up dialog box describes the action taken by Advanced EDR.
icon next to the action. A pop-up dialog box describes the action taken by Advanced EDR. -
Click Do not detect again. Advanced EDR performs these actions:
-
Allows the item to run on all computers managed by the administrator. With exploits, you allow the execution of the specific exploit technique that was used on the specific vulnerable program.
-
Allows all libraries and binary files used by the program to run, except those already known and classified as threats.
-
Adds the item to the Programs allowed by the administrator list.
-
Stops generating incidents for the item in the Malware, PUP, and Exploit panels.
-
Stopping detecting a network attack
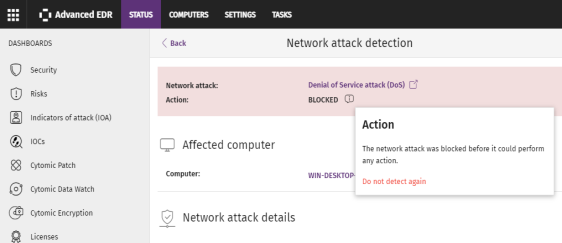
If you do not consider the traffic blocked a threat, you can create an exclusion for the source IP address and the type of attack.
The exclusion applies to all computers managed by Advanced EDR.
To stop blocking an item and create an exclusion for Network Attack activity:
-
From the top menu, select Status. From the side panel, select Security.
-
Click the Network Attack Activity panel. Select the type of network attack you want to allow.
-
On the details page, click the icon next to the action. A pop-up dialog box describes the action taken by Advanced EDR.
-
Click Do not detect again. The Do not detect again box opens. It shows the type of attack and the source IP address.
-
In Allow this type of network attack only from the following IPs text box, enter the source IP addresses from which you want to allow inbound traffic for the attack type. You can enter individual IP addresses separated by commas or IP address ranges separated by a dash. If you want to allow any IP address to send traffic of the specified attack type, leave the text box empty.
-
Click Do not detect again. Advanced EDR performs these actions:
-
Allows inbound traffic corresponding to the attack type to enter the network if the source IP address is on the list.
-
Stops generating detections for this traffic.
-
Includes the attack type in the Detected items allowed by the administrator list list.
-
Stopping allowing the execution of previously allowed items
To block a previously allowed item again:
-
From the top menu, select Status. From the side panel, select Security.
-
In the Detected items allowed by the administrator list, click the
 icon to the right of the item that you want to stop allowing to run.
icon to the right of the item that you want to stop allowing to run.
Advanced EDR performs these actions:
-
Removes the item from the Detected items allowed by the administrator list.
-
Adds an entry to the History of items allowed by the administrator list. The Action column shows Exclusion removed by the user.
-
Adds the item back to the corresponding list:
-
Malware activity
-
PUP activity
-
Exploit activity
-
Threats detected by the antivirus
-
Network attack activity
-
-
Resumes generating incidents for the item.
-
If the item is an unknown item in the process of classification, it reappears in the Currently blocked programs being classified list.