List of allowed threats and unknown programs
You have multiple panels and lists available to get information about programs that you allow which Advanced EDR initially prevented from running:
-
The Detected items allowed by the administrator panel.
-
The Detected items allowed by the administrator list.
-
The History of items allowed by the administrator list.
Detected items allowed by the administrator
This panel shows the number of items the administrator allows which Advanced EDR initially prevented from running. These items were considered a threat or are unknown files under classification.
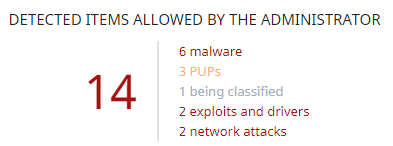
Meaning of the data displayed
The panel shows the total number of items excluded from blocking, broken down by type:
Lists accessible from the panel
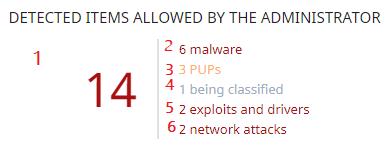
Click the hotspots in Zonas activas del panel Elementos detectados permitidos por el administrador to open the Detected items allowed by the administrator list list with these predefined filters:
Detected items allowed by the administrator list
This list shows all items the administrator allows which Advanced EDR considered a threat.
| Field | Description | Values |
|---|---|---|
|
Classification |
Type of threat that is allowed to run. |
|
|
Threat |
Name of the item that is allowed to run.
|
Character string |
|
Details |
Name of the file that contains the threat.
|
Character string |
|
Hash |
String that identifies the file. This is empty if it is an exploit or network attack. |
Character string |
|
User name |
Console user account that added the item exclusion. |
Character string |
|
Date allowed |
Date the event took place. |
Date |
|
Delete |
Removes the item exclusion. |
|
Fields displayed in the exported file
Filter tool
| Field | Description | Values |
|---|---|---|
|
Search |
|
Enumeration |
|
Classification |
File type the last time it was classified. |
|
|
Original classification |
Original classification of the file when it was allowed to run. |
|
History of items allowed by the administrator list
This list shows a history of all events related to threats and unknown files in the process of classification that the administrator allowed to run. This list shows all classifications that an item has gone through, from the time it entered the Detected items allowed by the administrator list until it left it, as well as all other classifications caused by Advanced EDR or by you.
This list does not have a corresponding panel. You must access it through the History button in the upper-right corner of the Detected items allowed by the administrator page.
| Field | Description | Values |
|---|---|---|
|
Classification |
Type of threat that is allowed to run. |
|
|
Threat |
Name of the item that is allowed to run.
|
Character string |
|
Details |
Name of the file that contains the threat.
|
Character string |
|
Hash |
String that identifies the file. This is empty if it is an exploit or network attack. |
Character string |
|
Action |
Action taken on the allowed item.
|
Enumeration |
|
User name |
User account which triggered the change to the allowed file. |
Character string |
|
Date allowed |
Date the event was logged. |
Date |
Fields displayed in the exported file
| Field | Description | Values |
|---|---|---|
|
Details |
Name of the file that contains the threat.
|
Character string |
|
Current type |
Current classification of the threat that is allowed to run. |
|
|
Original type |
Classification of the threat that is allowed to run when it was initially detected. |
|
|
Threat |
Name of the malware or PUP that is allowed to run. If it is an unknown item, the column shows the file name. If it is an exploit or network attack, the exploit technique used appears. |
Character string |
|
Hash |
String that identifies the file. If it is an exploit or network attack, this field is blank. |
Character string |
|
Action |
Action taken on the allowed item.
|
Enumeration |
|
User name |
Console user account that added the item exclusion. |
Character string |
|
Date allowed |
Date the event took place. |
Date |
Filter tool
| Field | Description | Values |
|---|---|---|
|
Search |
|
Enumeration |
|
Classification |
File type the last time it was classified. |
|
|
Original classification |
Original classification of the file when it was allowed to run. |
|
|
Action |
Action taken on the allowed item.
|
Enumeration |