Computer details
When you select a device from the list of computers, a page opens and shows details of the hardware, software, and security settings of the computer.
To show or hide the general details section and notifications, click ![]() or
or ![]() .
.
The details page is divided into these sections:
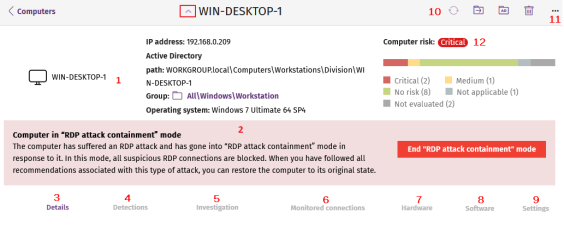
-
General (1): Information to help you identify the computer.
-
Notifications (2): Notifications that might indicate potential problems.
-
Details (3): Lists a summary of the hardware, software, and security settings of the computer.
-
Detections (4): Indicates the security status of the computer.
-
Investigation (5): Opens the Cytomic Orion investigation console and lists the telemetry collected for the computer. See Investigation section (5). Requires the Access Advanced Telemetry permission. See Understanding permissions.
-
Monitored connections (6): Lists the inbound connection attempts from remote computers. See Endpoint Access Enforcement settings options.
-
Hardware (7): Lists hardware installed on the computer, its components and peripherals, as well as resource consumption and use.
-
Software (8): Lists software packages installed on the computer, as well as versions and changes.
-
Settings (9): Lists security settings and other settings assigned to the computer.
-
Toolbar (10): Includes buttons for each action you can take for managed computers.
-
Hidden icons (11): Based on the size of the window, some of the actions are available from an options menu.
-
Computer risk (12): Risk information for the computer, including the risk level. See Risk assessment module lists.