Cytomic Orion Benefits
Cytomic Orion is a service for specialized security analysts. Its key benefits are:
-
Proactive and automated search for advanced threats and cyberattacks that do not use malware to achieve their goals, thereby making their detection through conventional security tools more difficult.
-
Search for TTPs (tactics, techniques, and procedures) used by hackers.
-
Early detection of attacks before they can achieve their goals.
-
Ability to establish response measures against detected threats, including containment of security breaches, rollback of changes made by attackers to computers on the network, and collection of evidence to perform forensic analysis tasks.
-
Seamless integration with the other tools used by SOCs.
Proactive Search for Advanced Threats
Cytomic Orion continuously monitors networks and searches for indicators under the premise that there is a permanent threat of attackers successfully ‘installing’ themselves on an organization network. It automatically creates hypotheses in the form of indicators that show the new evasion techniques and lateral movements detected, providing analysts with a starting point for more in-depth investigation to validate these hypotheses.
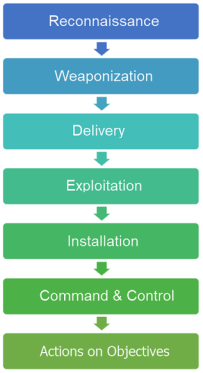
Early Detection of Attacks
Early detection of the attacker makes it possible to reduce the risk, accelerate containment capabilities, and reduce operational costs. Cytomic Orion can stop attacks in any of the phases defined in the cyber kill chain (CKC).
Search for TTPs
The ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework, developed by the MITRE Corporation, was created in 2015 as a living and growing document of the tactics and techniques used by hackers, resulting from researching millions of attacks on networks.
The MITRE Corporation’s goal is to coherently and clearly divide and classify attacks, facilitating their identification and detection. Most attackers use a combination of tactics and techniques to hide their lateral movements, discover and exploit system weaknesses, evade protection, and take advantage of weaknesses and non-secure settings on networks and computers.
Finding each one of these techniques during an ongoing attack is crucial in identifying which phase of the CKC the attacker is in. This streamlines the analysis and increases efficiency in collecting evidence that helps to identify a hacker’s goals and enables a company to develop a detailed response plan.
For this reason, the Cytomic Orion threat hunting rules match the techniques described in the ATT&CK framework, thereby facilitating their interpretation and accelerating the implementation of response mechanisms.
Response Measures
Incident response is a process made up of a series of sequential steps led and taken by the CSIRT (Computer Security Incident Response Team), many of which are assisted by the remote remediation tool provided by Cytomic Orion:
Damage Containment and Risk Mitigation
Quick action can reduce the effects and severity of an attack. The aim of the containment phase is to protect an organization confidential information during the course of the attack without interfering with the tasks carried out by the incident response team. This includes protecting system files against loss or tampering that can result in prolonged service outage.
Identification of the Type and Severity of an Attack
For an organization to recover effectively from an attack, it must be able to determine the severity of the risk that the computers on its network have been exposed to. To do that, organizations must be able to establish the nature, source, start date, and purpose of the attack, and identify which computers have been compromised and which files have been accessed by attackers.
Collection of Evidence
In many cases, if an organization suffers a targeted attack, it may be necessary to report it to the relevant law enforcement agencies. To do that, you must collect evidence of the attack: files tampered with, network traces, executed processes, as well as other information from compromised computers.
Recovery of Computers
How services are restored generally depends on the scope of the security incident. Any method must include action plans for dealing with deletion of files and processes, recovery of backups made prior to the start of the incident, etc.
Integration with SOC Tools
Cytomic Orion incorporates multiple APIs to facilitate integration with the other tools deployed at the SOC. This way, organizations can build a set of tools that provide these benefits:
-
Enable the SOC to provide a homogeneous response to the various types of incidents and situations it will face.
-
Minimize manual data exchange among the different tools implemented.
-
Automate repetitive tasks, enabling technicians to save time and effort that they can devote to more productive tasks.