Endpoint Access Enforcement module lists
Accessing the lists
Access the Endpoint Access Enforcement lists as follows:
-
From the top menu, select Status. From the side menu, select Endpoint Access Enforcement. Click any of the widgets.
-
From the top menu, select Status. From the side menu, click Add. A dialog box opens with the available lists. Select the Connections identified by Endpoint Access Enforcement list.
Required permissions
| Permission | Access to lists |
|---|---|
|
View detections and threats |
Connections identified by Endpoint Access Enforcement |
Connections identified by Endpoint Access Enforcement
This list shows the inbound connections received by computers on the network that meet the conditions configured in the Endpoint Access Enforcement settings. See Endpoint Access Enforcement settings options.
| Field | Description | Values |
|---|---|---|
|
Computer |
Name of the target computer. |
Character string |
|
Group to which the target computer belongs. |
Character string |
|
|
Remote computer |
Character string |
|
|
Risk detected |
Status of the connecting computer. |
|
|
Action |
The action that Advanced EDR took on the connection. |
|
|
Protocol/port of the connection. |
Numeric value |
|
|
Occurrences |
Number of times the connection was detected in one hour. |
Numeric value |
|
Date |
Date on which Endpoint Access Enforcement detected the connection. |
Date |
|
Context menu |
Shows an action menu:
|
Enumeration |
To view a graphical representation of the list data, see the Programs blocked by the administrator widget.
Fields displayed in the exported file
| Field | Description | Values |
|---|---|---|
|
Client |
Customer ID or name. |
Character string |
|
Computer type |
Type of device. |
|
|
Computer |
Name of the target computer. |
Character string |
|
Group |
Group to which the target computer belongs. |
Character string |
|
IP address |
Primary IP address of the target computer. |
Numeric value |
|
Risk detected |
Status of the connecting computer |
|
|
Protocol |
Protocol/port of the connection. |
Numeric value |
|
Action |
Action taken by Endpoint Access Enforcement on the connection. |
|
|
Local IP address |
IP address of the target computer. |
Numeric value |
|
Remote host name |
Name of the connecting computer. |
Character string |
|
Remote IP address |
IP address of the connecting computer. |
Numeric value |
|
Local port |
Connection port on the target computer. |
Numeric value |
|
Remote port |
Connection port on the connecting computer. |
Numeric value |
|
Date |
Date on which Endpoint Access Enforcement detected the connection. |
Date |
|
Occurrences |
Number of times the connection was detected in one hour. |
Numeric value |
Filter tool
| Field | Description | Values |
|---|---|---|
|
Search computer |
Search by computer name. |
Character string |
|
Computer type |
Filters by type of device. |
|
|
Dates |
Set a time period, from the current moment back. |
|
|
Action |
Filter by the action taken by Endpoint Access Enforcement on the connection. |
|
|
Risk detected |
Filter by the status of the connecting computer. |
|
|
Protocol |
Filter by the connection protocol. |
Character string |
Connection Details page
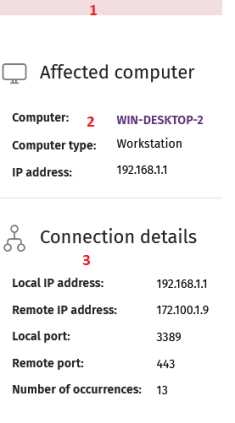
In the Connections Identified by Endpoint Access Enforcement list, click a line to open the Connection Details page. The page has three sections:
-
Computer alerts (1): Shows details of the alert generated by the target computer.
-
Affected computer (2): Name, IP address, and type of the target computer.
-
Connection details (3): Summary of the local and remote IP addresses and ports used in the connection, and the number of times the connection was detected.
Computer alerts (1)
| Field | Description | Values |
|---|---|---|
|
Detection date |
Date the connection was detected. |
Date |
|
Risk detected |
Status of the connecting computer |
|
|
Protocol |
Protocol/port of the connection. |
Numeric value |
|
Action |
Action taken by Endpoint Access Enforcement on the connection. |
|
|
Recommendations |
Recommendations for the security administrator of the target computer. |
Character string |
Affected computer (2)
| Field | Description | Values |
|---|---|---|
|
Computer |
Name of the target computer. If you have permission to view the computer, click it to access the Computer Details page. See Computer details. |
Character string |
|
Computer type |
Type of device. |
|
|
IP address |
Primary IP address of the target computer. |
Numeric value |
Connection details (3)
| Field | Description | Values |
|---|---|---|
|
Local IP address |
IP address of the target computer. |
Numeric value |
|
Remote IP address |
IP address of the connecting computer. |
Numeric value |
|
Local port |
Connection port on the target computer. |
Numeric value |
|
Remote port |
Connection port on the connecting computer. |
Numeric value |
|
Occurrences |
Number of times the connection was detected in one hour. |
Numeric value |