Introduction to the various types of settings profiles
A security settings profile is a group of settings for a specific security area that you use to configure the endpoint security product and specify how it operates on your network computers and devices. You assign profiles to one or more groups and all computers and devices in the groups receive the settings in the profile.
This is an introduction to the different types of settings profiles supported by Advanced EDR.
Advanced EDR enables you to configure these aspects of the service:
| Settings | Description |
|---|---|
|
Users |
Manage the user accounts that can access the management console, the actions they can take (roles), and their activity. For more information, see Accessing, controlling, and monitoring the management console. |
|
Per-computer settings |
Specify how often to install Advanced EDR updates on workstations and servers. You can also define settings to prevent tampering and unauthorized uninstallation of the protection software. For more information, see Configuring the agent remotely. |
|
Remote control |
Specify access to user computers from the Cytomic Orion threat hunting product. For more information, see Remote computer control. |
|
Network settings |
Specify the language of Advanced EDR installed on workstations and servers. You can also define the type of connection to the Cytomic cloud. For more information, see Configuring the agent remotely . |
|
Network services |
Specify how Advanced EDR communicates with computers on the network:
|
|
VDI environments |
Define the maximum number of computers that can be simultaneously active in a non-persistent virtualization environment. |
|
My alerts |
Configure alerts to send to the network administrator by email. For more information, see Alerts. |
|
Workstations and servers |
Define how Advanced EDR protects the computers on your network against threats and malware. For more information, see Security settings for workstations and servers. |
|
IOC gallery |
Import and export IOCs to and from the protection product and search protected computers for indicators of compromise. For more information, see Detection and management of IOCs. |
|
Indicators of attack (IOA) |
Detect sophisticated infection strategies that use multiple attack vectors and operating system tools for extended periods of times. For more information, see Indicators of attack settings. |
|
Program blocking |
Specify how Advanced EDR must behave to block the execution of certain programs. For more information, see Program blocking settings. |
|
Authorized software |
Prevent unknown programs in the process of classification from being blocked. For more information, see Authorized software settings. |
|
Specify when the protection software searches for new patches and software updates for the Windows operating systems and third-party applications installed across the network. For more information, see Cytomic Patch (Updating vulnerable programs). |
|
|
Endpoint Access Enforcement |
Monitor inbound connections to computers on the corporate network. Allow or block connections based on the security status of the connecting computer. For more information, see Endpoint Access Enforcement settings. |
|
Cytomic Data Watch |
Monitor the personal data stored on the storage systems on your network. For more information, see Cytomic Data Watch (Personal data monitoring). |
|
Encryption |
Encrypt the content of your computer internal and external storage devices. For more information, see Cytomic Encryption (Device encryption). |
| MDR |
Describe the customer IT infrastructure a partner must monitor and protect from malware attacks and external threats. These settings can be accessed only if the customer has purchased the MDR service from a partner. For more information, see MDR service settings. |
Modular vs. monolithic settings profiles
By supporting different types of profiles, Advanced EDR uses a modular approach to creating and deploying the settings you want to apply to managed computers. The reason for using this modular approach and not just a single, monolithic profile that covers all the settings is to reduce the number of profiles created in the management console. This in turn reduces the time that administrators have to spend managing the profiles created. Modular profiles are lighter than monolithic profiles, which would result in numerous large and redundant settings profiles with little differences between each other.
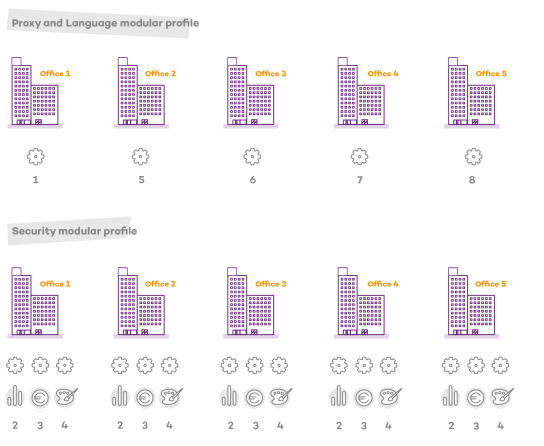
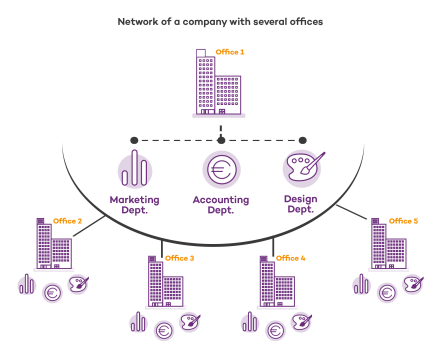
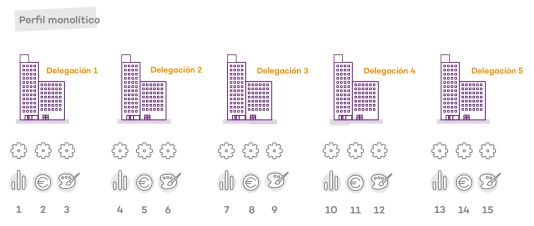
Case study: Creating settings profiles for multiple offices
This example uses a company with five offices, each with a different communications infrastructure and therefore different proxy settings. Also, each office requires three different security settings profiles: one for the Design department, one for the Accounting department, and one for Marketing.
Using monolithic profiles, the company would require 15 different settings profiles (5 offices x 3 security settings profiles in each office = 15) to adapt to the needs of all three departments in the company offices.
However, because Advanced EDR separates the proxy settings from the security settings, the number of profiles needed is reduced (5 proxy profiles + 3 department profiles = 8) as the security profiles for each department in one of the offices can be reused and combined with the proxy profiles in other offices.