Risk assessment settings
Required permissions
The risk assessment feature is visible to all users of the web console. However, you must have the Full Control role to configure it. For more information, see Managing roles and permissions. The risk assessment settings apply equally to all computers on the IT network.
Accessing the settings
From the top menu, select Settings. From the side menu, select Risks. The Risks page opens. This page is divided into two main areas: a list of risks and a series of drop-down menus to assign risk levels.
Risk list
Most risks have to do with the various types of settings implemented in Advanced EDR. Other risks are related to the security software status information sent by computers to the Cytomic servers.
The risks you can assess vary based on the operating system installed on the computer.
| Risk | Description |
|---|---|
|
No protection |
The computer has protection installation errors or does not have a license. See Protection status. |
|
Out-of-date protection |
The version of the protection engine installed on the computer is out of date. The computer is vulnerable to threats. See Details section (3). |
|
Out-of-date knowledge (more than 30 days) |
The version of the signature file installed on the computer is out of date. The computer is vulnerable to threats. See Outdated protection. |
|
No connectivity to knowledge servers |
Communications between the computer and the Cytomic servers have failed. The computer is not completely protected. To verify the computer meets the connection requirements, see Product features and requirements. |
|
No uninstallation protection |
The computer is not password protected to prevent unauthorized protection uninstallation or tampering. See Configuring security against protection tampering. |
|
Anti-tamper protection disabled |
The protection can be modified and tampered with. See Configuring security against protection tampering. |
|
Advanced protection is not active or reports threats but does not block or disinfect malware. See Advanced protection. |
|
|
The advanced protection settings allow execution of unknown programs already installed on user computers but block programs that originate from an external source. See Advanced protection. |
|
|
Advanced protection for Linux disabled or in Do not detect or Audit mode |
Advanced protection is not active or reports threats but does not block them. See Detect malicious activity (Linux computers only). |
|
Anti-exploit protection disabled or in Audit mode |
Anti-exploit protection is not active or reports detections but does not take action against them. See Anti-exploit protection settings. |
|
Folder, file, and extension exclusions |
There are files, folders, or extensions that are not scanned for malware.
|
|
Recent indicators of attack |
The computer reported the detection of indicators of attack (IOAs) in the last 30 days. See Managing indicators of attack. |
|
Critical patches pending installation |
The computer has Cytomic Patch installed and has reported the existence of critical patches that are pending installation. You can receive notification of this risk immediately or a specified number of days after the patches are published. By default, the number of days is 30, although you can edit this parameter when you enable this risk for evaluation. See Configuring the discovery of missing patches. |
|
Audit mode enabled |
The security software detects and reports threats, but it does not block or delete them. When you enable Audit mode in a settings profile, the overall status of the protection applied to the computers that receive the settings does not change. Audit mode does not change the configuration in the web console. See Audit mode. |
|
Network attack protection disabled or in "Audit" mode |
Real-time scanning of network traffic does not detect or stop lateral movements by fileless threats and advanced attacks that use exploits. See Network attack protection. |
How risk assessment works
Cytomic sets a default risk level for each risk. This is the risk level when you first open the Settings > Risks page. You can change the default risk level to another risk level, based on your needs.
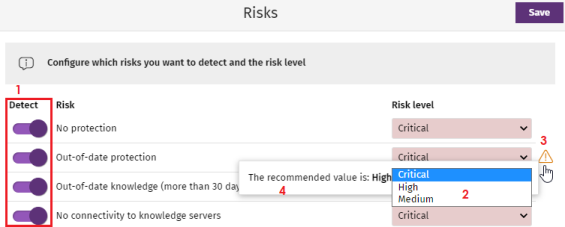
To configure risk assessment:
-
From the list of risks (1), click the toggles to enable the risks you want to detect.
-
From the Risk level drop-down menu (2), select a risk level for each risk: Critical, High, Medium.
If the risk level you select does not match the level recommended by Cytomic, the
 icon (3) appears. Point the mouse to the icon. A message appears (4) that shows the risk level recommended by Cytomic.
icon (3) appears. Point the mouse to the icon. A message appears (4) that shows the risk level recommended by Cytomic. -
Click Save.
Risk update is asynchronous. There could be a delay between when you configure risks and when data shows in lists and widgets.
Setting a risk level for recent IOAs
When you enable the Recent indicators of attack risk, the risk is detected when the security software detects an indicator of attack (IOA) on a computer.
To set the risk level:
-
From the Risk level drop-down menu (2), select a risk level (Critical, High, or Medium).
-
From the Risk level drop-down menu (2), select the Risk of indicators of attack option. If you select this option as the risk level, then the overall risk level becomes equal to the highest risk level for any IOA detected on the computer.
The security software only detects IOAs that have not been previously archived or were detected less than 30 days ago.
Example:
25 IOAs detected —12 Low Risk, 12 Medium Risk, 1 High Risk. The overall risk level for Recent indicators of attack is High.
If you archive the high risk IOA or if there are unarchived IOAs after 30 days, the risk level is calculated again. The risk level is Medium.
Example:
25 IOAs detected — 2 Medium Risk, 23 Low Risk. The overall risk level for Recent indicators of attack is Medium.
If you archive one of the medium risk IOAs, the risk level stays the same because there is another medium risk IOA. When you archive the remaining medium risk IOAs, the risk level changes to Low because the remaining, unarchived IOAs have a low risk level.
Monitoring risk assessment
Risk assessment results appear in the relevant widgets and lists. For more information, see Risk assessment module lists and Risk assessment module panels/widgets.
Modification and recalculation of recommended values
When Cytomic releases a new version of Advanced EDR, we might change the default risk level for risks. When you upgrade to a new version of Advanced EDR:
-
Risks that you did not modify the default risk level for automatically update to the new default value recommended by Cytomic.
-
Advanced EDR recalculates the overall risk level for all computers. The default configuration shows the new recommended risk levels.
Calculation of the overall risk level for a specific computer
The security software calculates the overall risk level for a specific computer when:
-
You upgrade to a new version of Advanced EDR.
-
The computer settings change, the computer or device moves from one group to another, a new computer or device registers, or the license assigned to the computer changes, in some cases.
The overall risk level assigned to a computer matches the highest risk level of the risks detected on it.
For example:
-
A computer has five risks. All of the them are active, one of which has a High risk level and the other four have a Medium risk level. The computer overall risk level is High.
-
A computer has five risks. Four risks are active (One has a High risk level and three have a Medium risk level) and one is inactive (with a Critical risk level). The computer overall risk level is High.
Managing exclusions
To avoid increasing the risk level for a computer when you add exclusions to the Workstations and Servers settings profile assigned to it, you can select which exclusions are taken into account to calculate the risk level.
Configuration
-
From the top menu, select Settings. From the side menu, select Risks. The Risks page opens.
-
From the list of risks (1), enable the Folder, file, and extension exclusions risk.
-
Click the Manage exclusion impact link.
The Manage exclusion impact dialog box opens. This dialog box is divided into two areas:
-
The left area shows all of the file, folder, and extension exclusions added to all of the Workstations and Servers settings profiles created in the management console. These exclusions impact the security risk and are taken into account to calculate the risk level for your computers. See How risk assessment works and Calculation of the overall risk level for a specific computer.
-
The right area shows the exclusions you have selected to not impact the security risk status. These exclusions are not taken into account to calculate the overall risk level for your computers.
Use
 to move the exclusions you do NOT want to impact the security risk status to the right. Use
to move the exclusions you do NOT want to impact the security risk status to the right. Use  to move exclusions back to the left.
to move exclusions back to the left.-
Use the Control key to select multiple items at the same time. To select al items, click Select all.
-
Click Save.
Viewing exclusions
The number of exclusions you have selected to not impact the risk level for your computers appears on the risks status page. See Risk assessment module panels/widgets.
-