Queries Side Panel (1)
This panel provides access to the queries previously saved by analysts or created by Cytomic. It contains these elements:
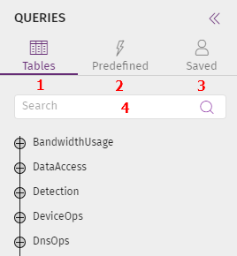
-
Tables (1): Contains the data model used by Cytomic Orion to organize the information collected from the monitoring of processes.
-
Saved (3): Contains SQL statements designed by the analyst and saved for frequent use sentences library organized in a tree structure and designed by Cytomic.
-
Predefined (2): Contains a tree of SQL statements created by Cytomic.
-
Search (4): Text box to quickly find queries.
Tables (1)
For more information about the meaning of the fields in the data model, see chapter Format of the Events Used in Cytomic Orion.
This tab shows the tables and fields available to the analyst to create their own queries. To speed up the process, click a field to automatically copy it to the Advanced SQL query panel in the position indicated by the cursor.
The Tables tab includes all the information collected from the client's IT infrastructure, organized into a number of tables that represent multiple techniques and actions frequently run by the processes in a cyberattack.
| Table | Description |
|---|---|
|
BandwidthUsage |
Volume of information handled in each data transfer operation performed by the process. |
|
DataAccess |
Contains an entry for each operation in which the process accessed data files hosted on internal mass-storage devices. |
|
Detection |
Contains an entry for each detection made by the Cytomic EDR active protections. |
|
DeviceOps |
Contains an entry for each operation in which the process accessed an external device. |
|
DnsOps |
Contains an entry for each operation in which the process accessed the DNS name server.. |
|
Download |
Contains an entry for each operation in which the process downloaded data. |
|
Evidence |
Contains an entry for each ungrouped indicator detected. |
|
Indicators |
Contains an entry with grouped indicators. For more information about how Cytomic Orion groups indicators, see Indicator Grouping. The Indicators table matches the indicator list that appears in the Cytomic Orion console. See Indicators List |
|
LoginOutOps |
Contains an entry for each login or logout operation performed by the user. |
|
NetworkOps |
Contains an entry for each network operation performed by the process. |
|
ProcessOps |
Contains events for processes that performed operations on the computer hard disk. |
|
RegistryOps |
Contains an entry for each operation in which the process accessed the Windows Registry. |
|
RemediationOps |
Contains detection, blocking, and disinfection events from the security solution installed on the workstation or server. |
|
ScriptOps |
Contains an entry for each operation performed by a script-type process. |
|
SystemOps |
Contains an entry for each operation performed by the Windows operating system WMI engine. |
|
UserNotification |
Contains an entry for each notification displayed to the user and response (if any). |
This table indicates the fields included in each table.
| Table | Fields |
|---|---|
|
BandwidthUsage |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, MUID, ClientId, EventType, ParentPid, ParentMd5, ParentDrive, ParentPath, ParentFilename, BytesSent, BytesReceived, LoggedUser, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime. |
|
DataAccess |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentPid, ParentMd5, ParentDrive, ParentPath, ParentFilename, ParentAttributes, ChildPath, ChildFilename, ChildAttributes, LoggedUser, Config, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime. |
|
Detection |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentMd5, WinningTech, DetectionId, Date, InsertionDateTime. |
|
DeviceOps |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, NotificationType, DeviceType, UniqueId, IsDenied, IdName, ClassName, FriendlyName, Description, Manufacturer, PhoneDescription, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime. |
|
DnsOps |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentCount, ParentPid, ParentMd5, ParentDrive, ParentPath, ParentFilename, FailedQueries, QueriedDomainCount, DomainList, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime. |
|
Download |
DateTime LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentMd5, ParentDrive, ParentPath, ParentFilename, ParentPid, ChildMd5, ChildDrive, ChildPath, ChildFilename, ChildUrl, LoggedUser, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime. |
|
Evidences |
EvidenceDateTime, TimeStamp, Muid, ClientId, HuntingRuleName, HuntingRuleId, HuntingRuleMode, HuntingRuleSeverity, HuntingRuleMitre, Details, InsertionDateTime. |
|
Indicators |
AlertDateTime, TimeStamp, Muid, ClientId, HuntingRuleName, HuntingRuleId, HuntingRuleType, HuntingRuleMode, HuntingRuleSeverity, HuntingRuleMitre, Details, Occurrences, PandaAlertId, InsertionDateTime. |
|
LoginOutOps |
DateTime LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, Actiontype, SessionType, ErrorCode, Username, Interactive, RemoteMachineName, RemoteIp, RemotePort, Times, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime. |
|
NetworkOps |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentPid, ParentMd5, ParentDrive, ParentPath, ParentFilename, Protocol, RemoteIp, RemotePort, LocalIp, LocalPort, Direction, LoggedUser, Ipv4Status, DetectionId, Hostname, Times, SocketOpFlags, ALProtocolExpected, ALProtocolDetected, CipherType, ConnectionState, ProxyConnection, ContentEncoding, TTPs, IOAIds, TelemetryType, Redirection, InitialDomain, Method, HeaderHttp, RuleId, Entropy, Date, InsertionDateTime. |
|
ProcessOps |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, Operation, ParentStatus, ParentMd5, ParentDrive, ParentPath, ParentFilename, ParentPid, ParentAttributes, ChildStatus, ChildMd5, ChildDrive, ChildPath, ChildFilename, ChildPid, ChildAttributes, ChildClassification, CommandLine, RemediationResult, Action, ServiceLevel, WinningTech, DetectionId, LoggedUser, RemoteIp, RemoteMachineName, RemoteUsername, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime, Key, Value, ValueData. |
|
RegistryOps |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentPid, ParentMd5, ParentDrive, ParentPath, ParentFilename, RegistryAction, Key, Value, ValueDataLength, ValueData, LoggedUser, Config, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime. |
|
RemediationOps |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentMd5, ParentDrive, ParentPath, ParentPid, ParentFilename, ChildMd5, ChildSha256, ChildDrive, ChildPath, ChildFilename, CommandLine, WinningTech, DetectionId, Action, RemediationData, RemediationResult, ServiceLevel, RemoteIp, RemoteMachineName, RemoteUsername, LoggedUser, ExploitOrigin, Url, ChildClassification, NapOriginIp, NapOriginPort, NapDestinationIp, NapDestinationPort, NapDirection, NapOccurrences, NapAttack, AttackerDeviceId, Risk, RuleId, Date, InsertionDateTime. |
|
ScriptOps |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentMd5, ParentDrive, ParentPath, ParentFilename, ParentPid, ParentAttributes, ChildMd5, ChildDrive, ChildPath, ChildFilename, ChildAttributes, ChildFileSize, ChildClassification, CommandLine, ServiceLevel, LoggedUser, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime. |
|
SystemOps |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, Type, ObjectName, CommandLine, MachineName, Username, IsLocal, ExtendedInfo, ChildMd5, RemoteMachineName, RemoteIp, IsSessionInteractive, Times, TTPs, IOAIds, TelemetryType, Date, InsertionDateTime, ParentPid. |
|
UserNotification |
DateTime, LocalDateTime, PandaTimeStatus, TimeStamp, Muid, ClientId, EventType, ParentMd5, ParentDrive, ParentPath, ParentFilename, ChildMd5, ChildDrive, ChildPath, ChildFilename, ChildClassification, ChildFirstSeen, WinningTech, DetectionId, RemediationResult, BlockReason, ServiceLevel, Date, InsertionDateTime. |
Meaning of Date-type Fields
Cytomic Orion supports multiple date-type fields that help differentiate the source of the data and prevent frequent errors that can occur when analysts work with events:
-
TimeStamp: Actual UTC date in epoch format (number of seconds that elapsed since 00:00:00 UTC on 1 January 1970) when the event occurred on the client’s computer. This date originates from an internal calculation in Cytomic Orion. It might not match the date on the computer where the event was logged if the latter is misconfigured.
-
DateTime: The same as TimeStamp but in Date:Time format.
-
Date: The same as TimeStamp but in Date format.
-
LocalDateTime: The computer date (in UTC format) at the time the logged event occurred. This date depends on the computer settings. As a result, it can be incorrect.
-
PandaTimeStatus: Contents of the DateTime, Date, and LocalDateTime fields:
-
0: Actual date not supported because it is an old event.
-
1: Actual date, supported but obtained by means of a calculation because the Cytomic server was unavailable.
-
2: Actual date provided by the Cytomic server.
-
-
InsertionDateTime: Date in UTC format at the time Cytomic logged the event sent by the computer on the company servers. This date is always later than the other dates because the events are queued to be processed.
Predefined (2)
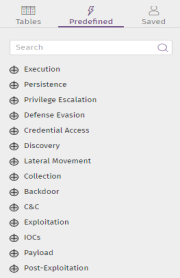
This tab shows the query library created by Cytomic. This library is divided into 14 groups and sub-groups that represent the MITRE tactics and techniques most frequently seen in a cyberattack or an infection.
Double-click a group to show the nodes, sub-nodes, and the predefined queries below it. Double-click a query to load it into the Advanced SQL query panel along with its name and description.
Predefined queries cannot be edited, but they can be copied and then edited by analysts. See Query Management Bar (1).
This table shows the available groups and a general description of the types of predefined queries they contain:
| Group | Description |
|---|---|
|
Execution |
Shows the execution of processes suspected of belonging to an attack because they are used in a different way than usual: unusual parameters, execution of PowerShell, AutoIt, or WMI scripts, etc. |
|
Persistence |
Shows the execution of actions by processes that try to gain persistence on the affected computer to survive system reboots. |
|
Privilege Escalation |
Shows actions taken to obtain more elevated permissions than those inherited based on the initial execution context. |
|
Defense Evasion |
Shows actions taken to evade defenses established by the network administrator, such as bypassing the local firewall, stopping the installed antivirus process, exploiting the SMB protocol to cause infections, etc. |
|
Credential Access |
Shows unauthorized access to the computer SAM to get user credentials. |
|
Discovery |
Shows actions taken to collect information through programs such as |
|
Lateral Movement |
Shows actions taken to spread the malware to other computers on the network to collect information and maximize a hacker chances of success. |
|
Backdoor |
Shows backdoor installation attempts to remotely access computers. |
|
Exploitation |
Shows attempts to exploit vulnerable processes. |
|
IOCs |
Shows processes that run known IOCs (Indicators of Compromise). |
|
Payload |
Detects the execution of Bitcoin mining programs. |
|
Post-Exploitation |
Shows processes that take actions which usually occur after a vulnerable process has been exploited (create users, stop services, etc.). |
|
PUPs |
Shows typical actions taken by processes classified as PUP (potentially unwanted programs). These actions usually correspond to the installation of browser toolbars and similar resources to show ads on clients’ computers. |
Saved (3)
This tab includes all the queries the analyst has created and saved over time. These queries are visible to the user accounts created in each MSSP/MDR vendor or SOC individually. Therefore, they are not shared among the different MSSPs/MDR vendors.
Saved queries are grouped by the type and sub-type you chose when you created them, giving rise to a tree structure which analysts can search easily to find a specific query.