From a Newly Created or Ongoing Investigation
To analyze an item belonging to an investigation:
-
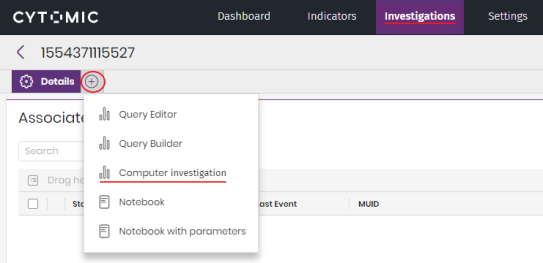
in the top menu, select Investigations. Create a new investigation. In the toolbar, click the
icon. Select Computer investigation. A dialog box opens where you can enter the details of the computer you want to analyze and the dates for the investigation.
-
Select a checkbox depending on the item you want to investigate:
-
MUID
-
MD5
-
MUID + MD5
-
Computer name
-
-
Enter the required information depending on the item you selected. The following sections detail the type of data required.
Computer Investigation: MUID
-
Enter the unique identifier of the computer you want to analyze, the time period for the investigation (maximum 48 hours), and the time zone for the period. To speed up the selection, click the MUID text box. A list opens that shows all compatible entities of interest created in the investigation. You can also enter an MUID directly.
-
If you do not know the computer MUID, see Tool for Converting a Computer Name to an MUID.
-
Click OK. A new tab is created that shows the computer name and its MUID in parenthesis. This tab contains the events found on the selected computer during the specified period.
File Investigation: MD5
-
Enter the hash of the file you want to investigate. To speed up the selection, click the MD5 text box. A list opens that shows all compatible entities of interest created in the investigation.
-
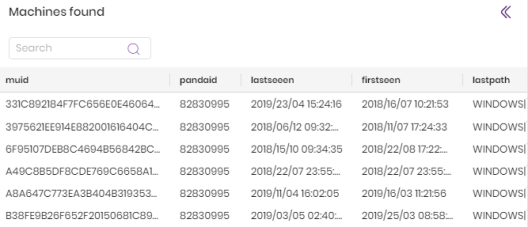
Click OK. A new tab is created that shows the file MD5. This tab contains the Found computers panel, which shows a list of all computers that have generated events associated with the target file MD5, as well as the date on which the events occurred and this information:
-
MUID: The unique identifier of the computer where the events related to the file MD5 occurred.
-
Pandaid: The unique identifier of the client to which the computer belongs.
-
Lastseen: The date on which an event that involves the file MD5 found on the selected computer was last logged.
-
Firstseen: The date on which an event that involves the file MD5 found on the selected computer was first logged.
-
Lastpath: The last logged path of the item found on the computer.
At the top of the panel, you can see a tool area:
-
Search: A filter tool that enables you to type only a partial string. Searches are performed on the content of all columns in the list.
-
Number of results: Number of entries shown in the list.
Investigation of a File on a Computer: MUID and MD5
-
Enter the unique identifier of the computer and the hash of the file you want to investigate. To speed up the selection, click the MUID and MD5 text boxes. A list opens that shows all compatible entities of interest created in the investigation. You can also enter an MUID and an MD5 directly.
-
If you do not know the computer MUID, see Tool for Converting a Computer Name to an MUID.
-
Click OK. A new tab is created that contains the Found computers panel, which shows a list of all computers that have generated events associated with the target file MD5, as well as the date on which the events occurred. See File Investigation: MD5.
Computer Investigation by Name
-
Enter the name of the Windows computer you want to analyze, the time period for the investigation, and the time zone for the period.
-
Select the client to which the computer belongs, because a computer name could belong to multiple clients.
-
Click OK. A new tab is created that shows the computer name and its MUID in parenthesis. This tab contains data for the selected computer during the specified period.